Dealing with Malware for Ordinary Users
The countermeasures of Malicious Ware (malware) are mitigation (prevention) or treatment like any other measures to cope against harmful substances. To prevent virus/worm infection is either we put up security to defend ourselves or avoid interacting with malwares. If we are already infected then we have cure the infection. This is the second assignment from my Masters Advanced Network Security Course which has never been published anywhere and I, as the author and copyright holder, license this assignment customized CC-BY-SA where anyone can share, copy, republish, and sell on condition to state my name as the author and notify that the original and open version available here.
1. Mitigation

This step is the most commonly used and mostly for those with the preference who are not expert in the area of malware. People usually know of the existence of malware and follows advices given by the media, experts, or computer companies to install firewalls, antivirus and antimalware softwares, and other preventive softwares. Finally tells them to update their Operating System (OS) (windows update for example), macrowares (word, spreadsheet), and other softwares to their latest version. Analogically equipped themselves with weapons and armors.
2. Evasion
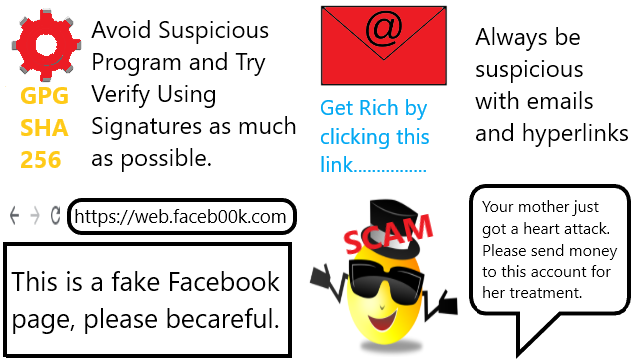
This step if you have better knowledge of malwares. Initially know the overview of how malwares works. (1) Like virus needs a host to run, resides on infected files, and can only initiate if you activate it. For this we will be careful when handling files by checking its size, its origin, its name, especially its format which virus resides in executeable formats. If it seems suspicious we should delete the file. If the system is modified, deleted, or a process occur without your approval is likely virus infected. (2) Other than virus a malware called worm exists, unlike virus it can infect a host without us executing it. In real life a worm can get inside of our body just getting contact in contaminated water. Virus cannot live without a host but worm can. In computer network is similar, even without your presence it keeps reproducing itself throught the network. Back then just by visiting a site or a mail server can already be infected with a worm. The network traffic could feel really heavy, or you might send informations to addresses you don't even recognize. If the site seems suspicious or receive a suspicious email, don't visit or open it. (3) Another dangerous malware that could take full control of your PC is a trojan horse. Back in the ancient Greeks this method was described as giving a large horse figure statue to the city of Troy during the Trojan war. Without any suspicion the city accepted the horse statue. What leads to the city's subjugation they didn't know there were soldiers inside the horse, and during the night those soldiers came out and took over the city. So in computers don't accept and execute suspicious files. (4) If already an expert, some says no need for antivirus. For example just use Linux or other OS other than Windows since most malwares are coded to attack Windows, using other system won't initiate the malware since the code doesn't match. This isn't everything and more measures are necessary.
3. Treatment
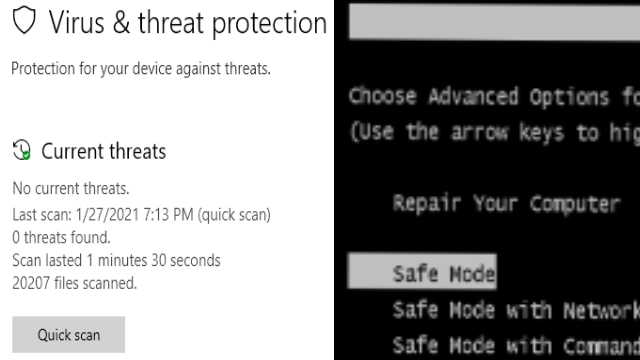
if already infected then we have to treat the infection or remove it. First is identification to make sure if it really is an infection and it's not a hardware problem. When it is sure that is not hardware problem, identify the symptoms, whether the process is heavy, high memory consumption, heavy traffic, a program runs without your approval, etc. Don't forget to disconnect from the network (unless performing an online scan). For common people usually install an antivirus, perform a scan and clean. But this method is not guaranteed since it is perform on an infected host. The best way to do this is to get another clean PC with the latest software and antivirus update and perform a scan on the disk of the infected host. If you're really an expert then you can remove it manually by booting into safemode or input the disk into a different operating system, then delete the files and registries of the infection.
4. Last Resort
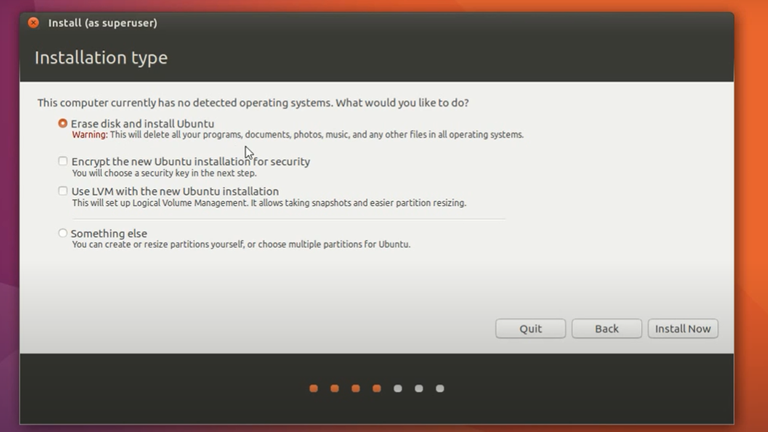
If all else fails the extreme resort is to destroy everything (along with the malware) and start again from a scratch. Reinstall your OS and have a fresh start (you may backup your data beforehand).
Mirrors
- https://www.publish0x.com/fajar-purnama-academics/dealing-with-malware-for-ordinary-users-xervoxz?a=4oeEw0Yb0B&tid=hive
- https://0darkking0.blogspot.com/2021/01/dealing-with-malware-for-ordinary-users.html
- https://0fajarpurnama0.medium.com/dealing-with-malware-for-ordinary-users-42fbb0bae40b
- https://0fajarpurnama0.github.io/masters/2020/07/07/dealing-malware-ordinary-users
- https://hicc.cs.kumamoto-u.ac.jp/~fajar/masters/dealing-malware-ordinary-users
- https://0fajarpurnama0.wixsite.com/0fajarpurnama0/post/dealing-with-malware-for-ordinary-users
- http://0fajarpurnama0.weebly.com/blog/dealing-with-malware-for-ordinary-users
- https://0fajarpurnama0.cloudaccess.host/index.php/9-fajar-purnama-academics/192-dealing-with-malware-for-ordinary-users
- https://read.cash/@FajarPurnama/dealing-with-malware-for-ordinary-users-a1f18acf
- https://www.uptrennd.com/post-detail/dealing-with-malware-for-ordinary-users~ODU2NTE2
Your post has been voted as a part of Encouragement program. Keep up the good work!
Try https://ecency.com and Earn Points in every action (being online, posting, commenting, reblog, vote and more).
Boost your earnings, double reward, double fun! 😉
Support Ecency, in our mission:
Ecency: https://ecency.com/proposals/141
Hivesigner: Vote for Proposal