Course: IP Version 4 Addressing And Subnetting Deep Dive (Part 8)
Hello and welcome, I am currently working on a video course 'addressing' IP version 4, and I've decided to post my slides and scripts here on STEEM as I go along. I appreciate any feedback or suggestions, or if you are new to the world of computer networking, I hope you enjoy them!
Here is part 8 of a multi-part series. How many parts will there be? I have no idea because I am posting them as I go along, but we are getting close to the end! In this part we will discuss how to determine if two hosts are on the same subnet, and other concepts like supernets, and wildcard masks.
If you missed any sections, click one of the links below for your favorite front end:
PART 1:
https://steempeak.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-1
https://steemit.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-1
https://busy.org/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-1
PART 2:
https://steempeak.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-2
https://steemit.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-2
https://busy.org/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-2
PART 3:
https://steempeak.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-3
https://steemit.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-3
https://busy.org/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-3
PART 4:
https://steempeak.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-4
https://steemit.com/palnet/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-4
https://busy.org/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-4
PART 5:
https://steempeak.com/stem/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-5
https://steemit.com/stem/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-5
https://busy.org/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-5
PART 6:
https://steempeak.com/stem/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-6
https://steemit.com/stem/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-6
https://busy.org/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-6
PART 7:
https://steempeak.com/stem/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-7
https://steemit.com/stem/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-7
https://busy.org/@joshman/course-ip-version-4-addressing-and-subnetting-deep-dive-part-7

At some point you may look at two addresses and assume they are on the same network. Take these two. They look pretty close right? But are they on the same network? Let’s find out!

If we line up both addresses an subnet mask and covert them to binary, we can see the first 3 octets match exactly (in blue), and the last octet is where the subnetting is taking place. We can then determine the subnet ID (in red) and the host ID (in white). You can immediately see that the subnet IDs do not match! This means these two hosts do not exist on the same network! They could not communicate without using a router.
If you ever experience two smaller similarly looking subnets that cannot communicate with each other, this could be the reason. Let’s take a look at some more examples.
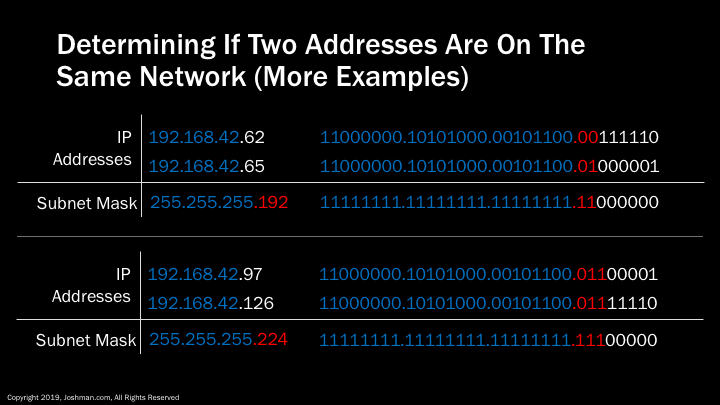
In the first example, we have a two /26 addresses. You can see from the subnet mask and subnet ID, they are on different networks.
In the second example we have two /27 addresses. We can see that the subnet IDs match, therefore they are on the same network and can communicate directly
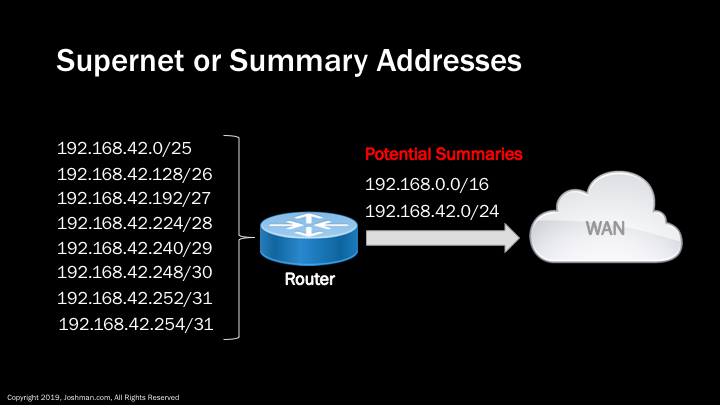
A supernet, or summary is simply the combination of two or more addresses into a single address. They are commonly used by routing protocols to simplify routing information, and also hide the internal addressing scheme of a network. In our example we have 8 distinct IP subnets behind a router. The router only needs to advertise a single summary or supernet to the Wide Area Network (WAN). Depending on the requirements, the summary can be more or less specific. Here we have two potential summaries, the /24 one is more specific. The /16 summary is less specific and encompasses the actual /24 behind the router, and an additional 255 /24 addresses that are members of the 192.168.0.0/16. In most cases having a more specific summary is better. A deeper understanding of summarization is needed for IP routing, but is beyond the scope of this course
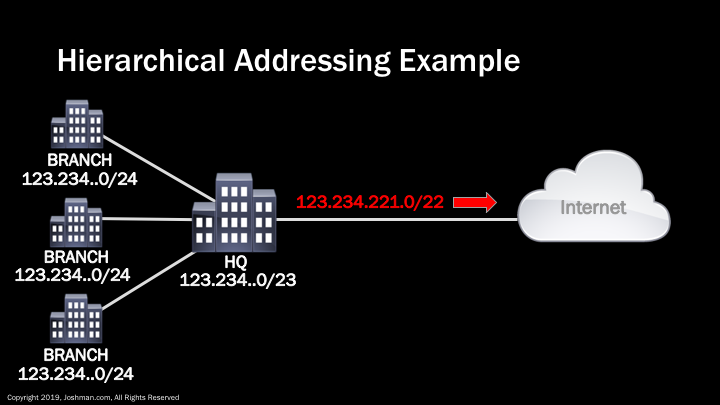
We’ve already touched on the concept of hierarchical addressing. Let’s take a look at a real world example that also ties in the concept of summarization. An internet service provider (ISP) has allocated a /22 network to an enterprise. The enterprise advertises a /22 summary to the ISP, but breaks up the allocation into 4 distinct networks. These include a /23 for the headquarters locations, and a /24 for each branch office. On the public Internet, outside networks are only aware of the /22 summary, and do not have any visibility of the hierarchical network design of the enterprise. This hierarchical design allows the enterprise to logically allocate their IP addresses and simplify their IP routing.
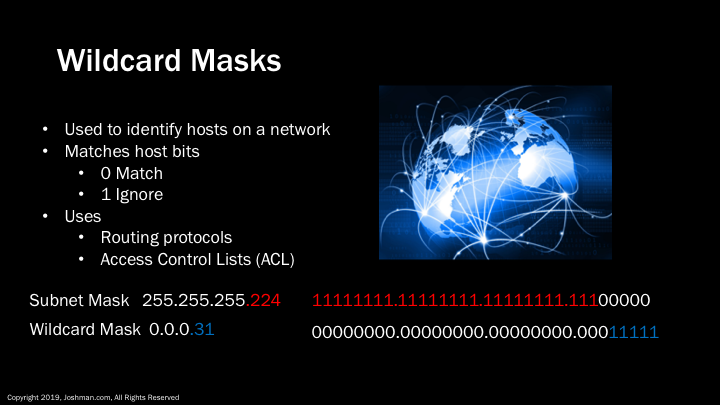
A wildcard mask, also called a hostmask, is a method to identify a range of host addresses on a network. Zeros in the wildcard mask need to be an exact match, while the ones can be any value. Wildcard masks are typically used in routing protocols, and also access control lists (ACLs). The most popular wildcard mask is simply an inversion of the subnet mask. You can see in this example, we have a /27, which leaves five bits for the wildcard mask. Both are broken down into binary.
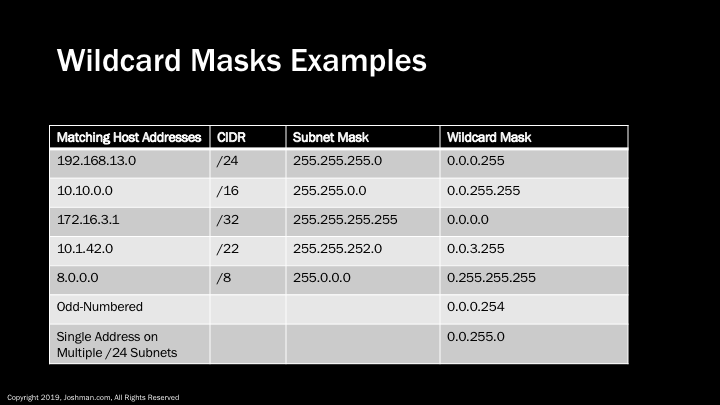
Here are some examples of using a wildcard mask to identify all hosts on a particular network. You can see from the table we are just taking all the zeros from the subnet mask, and setting them to one. We in turn take all of the ones from the subnet mask and setting them to zero. You can also identify a single host by setting a wildcard mask of all zeros.
You can also get creative with wildcard masks. For example, you can use them to match even or odd networks, or different networks that share a bit in common, such as a single host address on multiple subnets. This could be used to reduce the number of entries in an access control list.
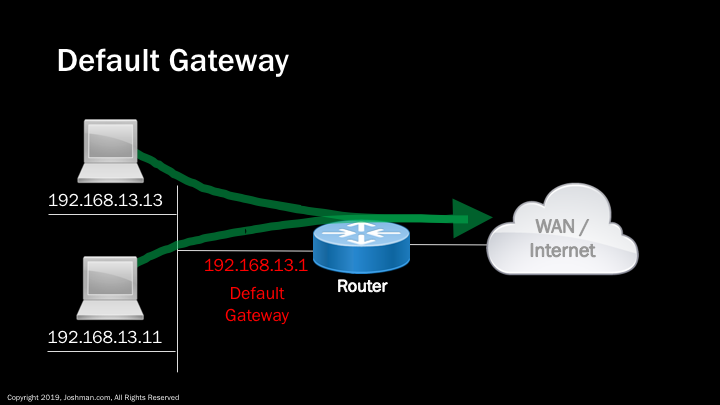
As promised, let’s describe the concept of a default gateway. If you are on a device trying to connect to a wide are network, or the Internet, you will need to hit a default gateway first. A default gateway is a device, such as a router, that provides an exit point from the local LAN. In our example, we have a pair of PCs on the same LAN. These PCs are able to reach each other directly, however if they need to get to the WAN or Internet, they will need send their traffic via the Default Gateway. Although a default gateway can be any IP address, it’s typically assigned from either the first IP address in the network, or the last one.
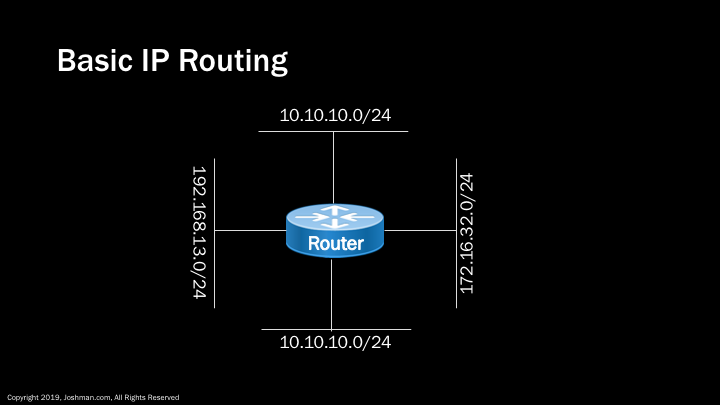
The concept of a default gateway leads us into the world of IP routing. Routing is beyond the scope of this course, but warrants a quick explanation. A router is simply a device that allows different networks to communicate. In the example we have 4 different networks connected to a router. The devices on each LAN can reach other devices on their respective networks, however they will require a router in order to communicate with devices on other networks. To communicate with other networks, these devices must do so via their local default gateway. Without the router in the middle, these individual networks would have no way to communicate with one another.
I want to quickly mention Network Address Translation (NAT) so you fully understand why private IP addresses can be used. NAT is the method by which a private RFC 1918 address can communicate to the public Internet, and has other uses as well. It simply translates from one address to another. There are multiple flavors of NAT. The most popular form is Port Address Translation (PAT), also called NAT overloading or Port overloading. It shares a single public IP address among multiple private IP addresses. It accomplishes this through manipulating TCP and UDP port numbers. This is the technology your home router uses.
Another form of NAT is static NAT. Static NAT creates a 1:1 relationship between a statically configured private IP address and the public IP address. The final form of NAT we will discuss is Dynamic NAT, dynamic NAT also creates a 1:1 relationship, but draws from a pool of available IP addresses.
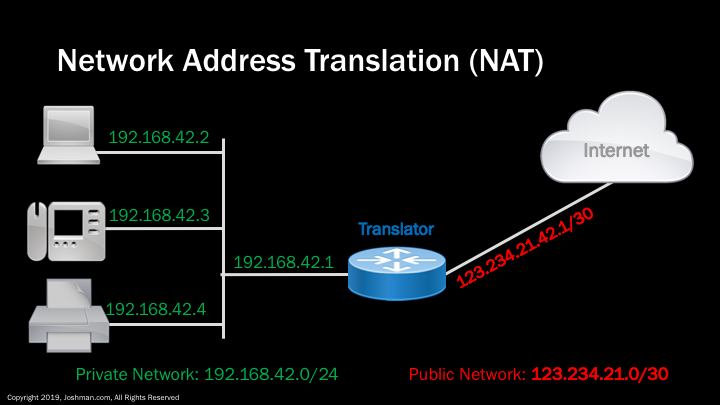
Just a quick example of NAT in action. On the left, we have a small office network with a PC, IP phone, and printer. The network has a router acting as a default gateway. All traffic destined for the Internet will hit this gateway. The router is configured for NAT, specifically Port Address Translation (PAT). The router receives a request for a service from the internal network destined for the Internet. It will automatically translate the IP address to the public address indicated in red. All devices on the internet network will share this single IP address. Each time a translation occurs, the router or translator will give the internet bound traffic a unique TCP or UDP port number. This lets multiple internal hosts use the same service with no conflicts.
Thanks for viewing. In the next part, we will go over how to determine your IP address under different operating systems, some basic tools for testing IP connectivity, and the future of IP.
Congratulations @joshman! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Lots of effort and brain power gone into this series, nice!
Thanks! Much appreciated.
This post has been voted on by the SteemSTEM curation team and voting trail. It is elligible for support from @curie.
If you appreciate the work we are doing, then consider supporting our witness stem.witness. Additional witness support to the curie witness would be appreciated as well.
For additional information please join us on the SteemSTEM discord and to get to know the rest of the community!
Thanks for having added @steemstem as a beneficiary to your post. This granted you a stronger support from SteemSTEM.
Please consider using the steemstem.io app to get a stronger support.