Ryuk, the ransomware that requires cryptocurrencies to companies and institutions in Spain

The ransomware that has affected consulting companies, town halls and radio networks in Spain is called Ryuk and comes from Russia. Malware can encrypt the computer database, spread on its own and attack business environments. The aim of the creators and broadcasters of this virus is to obtain a few bitcoins, extorting victims with the release of their computers.
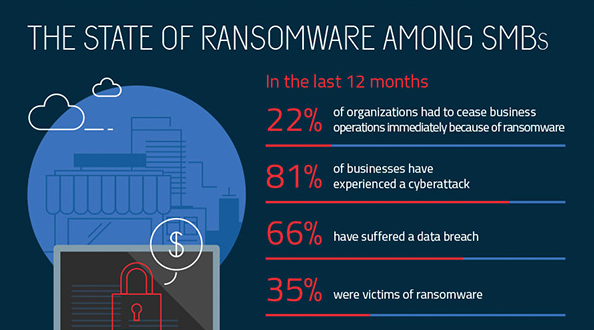
This November 4, a ransomware attack that affected the consulting company Everis and the multinational Prisa Radio. The National Cybersecurity Institute of Spain (INCIBE) does not have a specific number of Spanish companies affected by this virus. However, everything indicates that it is a planned attack that can spread easily.
Silent and highly lucrative
This ransomware, unlike the disastrous WannaCry and Petya, is not created to contaminate computers of common users. Ryuk's goal is business, says Sergio de los Santos, the cybersecurity specialist at Eleven Paths. "It's like a business product," says the expert, since hackers carry out planned attacks that are very difficult to detect.
The idea of hackers with this ransomware is not to affect thousands of computers, but a few companies that need their systems to operate. In this sense, minimum payments of 1.5 BTC have been reported to decrypt files and a maximum amount of 99 BTC per company. The fewer attacks are made and which systems are most vulnerable to ransomware are planned, the more lucrative Ryuk is for hackers, says De los Santos.

Ryuk's modus operandi is very similar to other ransomware, as it can be disseminated thanks to Trojans hidden in emails. Likewise, a new version of malware can spread by itself using the private networks of companies. To do this, it has a file known as Wake on LAN (WoL) that allows you to activate computers if they receive a remote order, thus expanding in a faster and quieter way.
If the virus manages to penetrate a vulnerable computer, it encrypts the entire database and does not give the key until the victim makes the payment. Because these are specialized attacks, hackers give their emails to negotiate the payment. Hackers also send the password to decrypt the files by email, after verifying that the transaction has been made in bitcoins.

Congratulations @thranax! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Vote for @Steemitboard as a witness to get one more award and increased upvotes!