PSA: This is what you can do with the exposed data from PDL customer...
This will be a short post. I just want to highlight a scam which is possibly crafted using the data exposed from the recent PDL customer incident and point out the severity of exposure of such seemingly non-sensitive data. I wrote about the incident a few days back and you might want to check out this post to learn more.

Source
This morning, a number of my colleagues received the following email. The email is from my "CEO" asking the colleague to help with an urgent errand.
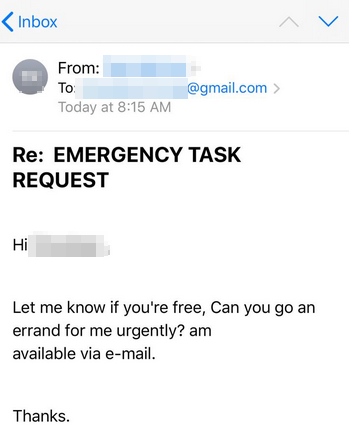
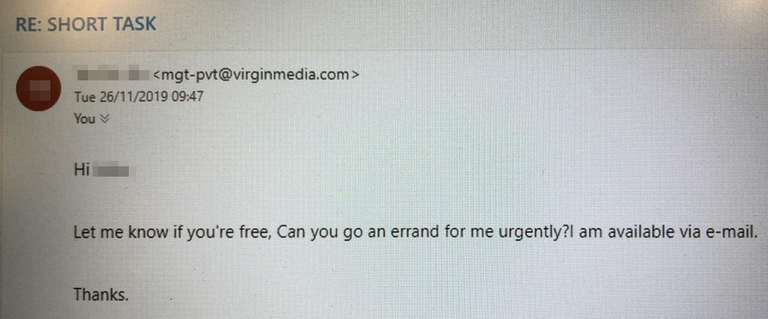
The above email is viewed from a mobile phone and the below sample is viewed from a PC,
Some learning points
A few things that I will like to point out. First, using the exposed data (job history, emails and phone numbers), it is extremely simple to craft realistic targeted emails to scam or phish someone. In this scam that my company received, the scammer is posing to be the CEO of my current company. Imagine if I craft an email pretending to be your previous employer and ask you to click a link to join the alumni event. Get you to create an account with a password and harvest it. If you reuse your password... BAM, I would have successfully taken over your other accounts.
Next, the scam email address is apparent when viewing on a PC, but when viewed on a mobile phone, it is much easier to trick someone. This is also true for phishing links. When viewing on a PC, it is easy to hover your mouse pointer over the link to check the actual URL. However on a phone, it is much more troublesome.
Finally, it is fortunate that our company do not allow syncing our corporate mailbox to personal email clients. The scam shown above will be even more effective if the user syncs work and personal mailboxes to a single email client. This makes it difficult for the user to detect that the email is actually sent to his/her personal mailbox even though it is a work related mail.
Conclusion
The data exposed is seemingly harmless, but it can be used for something much sinister. An elaborate phishing/scam attempt can be crafted with that amount of information and many people are at risk. Yet there is nothing much we can do once our data is out. It is also important to realize that in this incident, the data was exposed by accident, however, there are actually many organizations that purchased and owned these information about you legitimately. Businesses are monetizing your data while you are kept in the dark. Scary, isn't it?
10% of post rewards goes to @ph-fund and 5% goes to @steemstem to support these amazing projects.
The "Raise to 50" Initiative
Under 50 SP and finding it hard to do much on this platform? I might just be able to raise your SP to 50. Check this post to find out more!
This article is created on the Steem blockchain. Check this series of posts to learn more about writing on an immutable and censorship-resistant content platform:
- What is Steem? - My Interpretation
- Steem Thoughts - Traditional Apps vs Steem Apps
- Steem Thoughts - A Fat or Thin Protocol?
- Steem Thoughts - There is Inequitable Value Between Users and Apps
- Make my votes count! Use Dustsweeper!
- What caused STEEM to get dumped? Why I think the worst might be over
- Steem 2020 is about having a "SMART U"
hi @culgin
I just bumped into your post a moment ago. A bit to old to upvote :(
Perhaps you could share with us all your publications (which you would find valuable) on our "project hope" telegram channel. It would allow me to reach your post easier and share it with others within our group.
Cheers
Piotr
Thanks buddy. I try not to spam too much in the group. Keeping it to at most twice a week if possible. Haha..