How $50,000 saved MakerDAO from potentially losing all its collateral - A primer on bug bounty program
MakerDAO is a well-known brand in the DeFi industry. They are the governance body of the stablecoin, DAI. Unlike traditional banks which embrace fractional reserves, each DAI is minted with over-collateralization. In traditional finance, when $1 of credit is created, it is usually backed by less than $1 of collateral. In the current state of DeFi, especially for the case of MakerDAO and DAI, each DAI minted is backed by more than $1 worth of ETH. Interesting isn't it? But let's save this discussion on DeFi for another day and focus on today's topic.

Source
Since DAI are backed by ETH as collateral, the foundation of DAI is constructed on the collateral. If the collateral are gone, then DAI will be backed by nothing and it's value will therefore not remain stable. In fact, if all collateral are gone, DAI will basically go to zero.
Some background
It all started 3 months back when MakerDAO shared their plans for Multi-collateral DAI (MCD). The MCD was already planned and being developed in private for years but it was only 3 months ago that MakerDAO felt confident in sharing the details. As mentioned, ETH is currently the only supported cryptocurrency as collateral to create DAI. The MCD will allow more cryptocurrencies to act as collateral to mint DAI. This is a natural progression for the MakerDAO/DAI ecosystem and many have been anticipating this announcement.
Bug bounty
Most organizations with a mature cybersecurity/infosec program will typically use bug bounties to discover vulnerabilities on their systems. A bug bounty program, as its name suggests, basically rewards anyone who find significant bugs on the system and report them to the owner. The typical flow is as such:
- Organization starts a bounty
- Bounty hunters try to break the system and identify vulnerabilities
- Bounty hunters report vulnerabilities (if any)
- Organization assesses if vulnerability is valid and significant
- Organization agrees vulnerability is valid and fixes it
- Hackers validate the fix is effective
- Organization pays out the bounty to Bounty hunters. Bounty is typically proportionate to the severity of vulnerability (i.e. critical vulnerabilities get paid more)
- [Optional] Organization may choose to disclose the fixed vulnerabilities to the public
The process above are all done in private until the vulnerability is disclosed. A bug bounty program is an effective way to identify system vulnerabilities if done correctly. Imagine a decentralized pool of hackers working for you to fight for the bounty. This can be much more effective than engaging a single party to conduct a penetration test/source code review. However, the bounty must be good enough to attract proficient hackers to work on it. Internally, a strong infosec team is required to define clear scope and boundaries for such engagements and to assess the validity of reported vulnerabilities.
The MakerDAO case study
Using MakerDAO as a case study, let's run through the steps I mentioned in the previous section. MakerDAO hosts their bug bounty program on HackerOne. On the page, you will be able to see some useful information on how the program is setup.
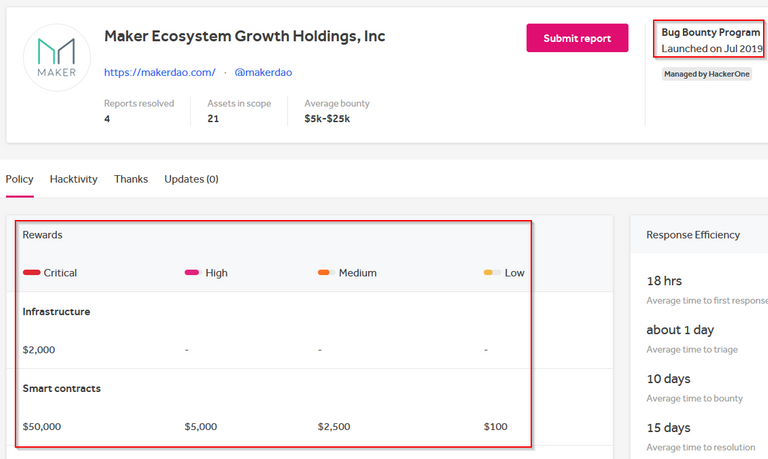
First, you will see that the program was launched on July 2019. Next the bounty amounts are provided. As mentioned before, the payouts will commensurate with the criticality of the vulnerability. In this case, $50k will be paid for any valid critical vulnerability on MakerDAO smart contracts.
If you scroll further down, you will be able to see more terms and conditions. I will not be explaining them in this post but do give it a read if you are keen.
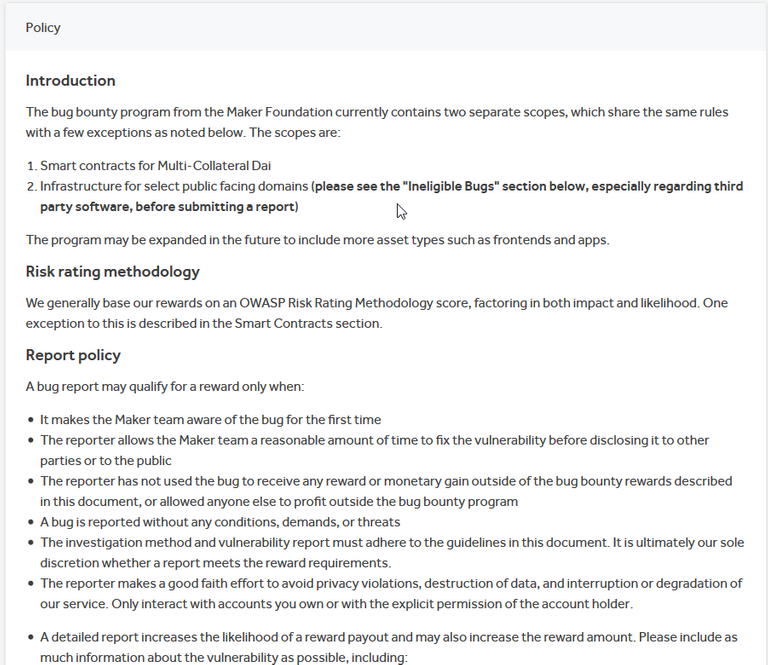
Once all these are furnished, we completed step 1! As you can see, the organization needs to have a mature infosec team to craft out these terms and conditions so that the program can be effective.
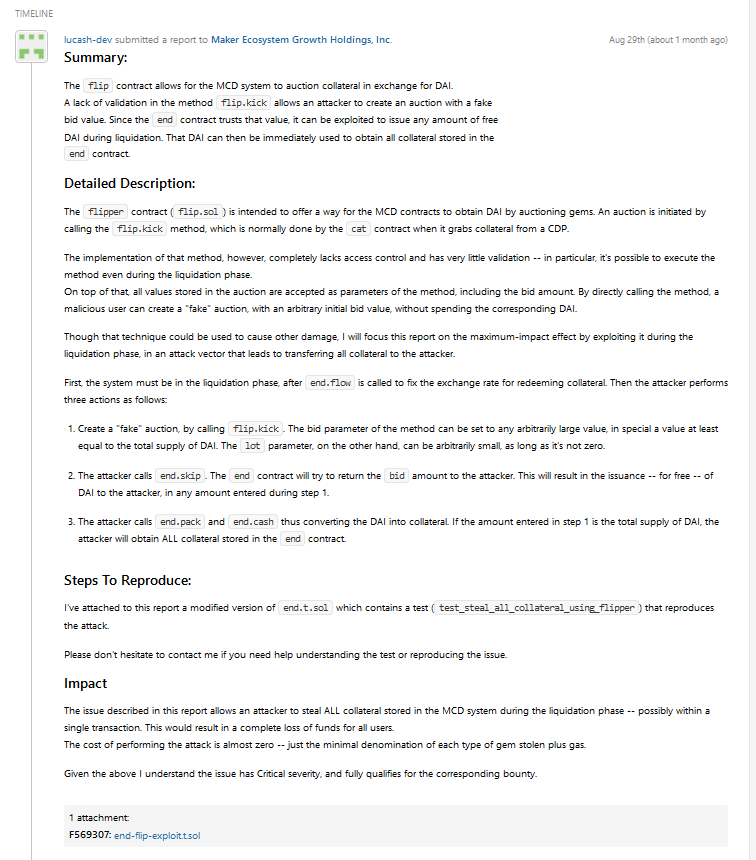
Step 2 is basically the hackers doing work in the background. Then comes Step 3, when a vulnerability is reported. For the case of MakerDAO, the vulnerability is eventually disclosed in this report. So, we will be able to see the chain of events.
Step 3 took place on 29th August, when the bounty hunter (lucash-dev) reported the vulnerability to MakerDAO. As part of the report, the bounty hunter will need to provide detailed impact analysis and steps to reproduce the issue. This bug is a critical vulnerability. As lucash-dev put it,
The issue described in this report allows an attacker to steal ALL collateral stored in the MCD system during the liquidation phase -- possibly within a single transaction. This would result in a complete loss of funds for all users.
The cost of performing the attack is almost zero -- just the minimal denomination of each type of gem stolen plus gas.
In other words, all collateral used in the new MCD smart contract can potentially be drained by an unauthorized party if this got deployed to the mainnet without the patch. I am not sure if this would have affected existing ETH collateral, but it will certainly affect new collateral put in as part of MCD. We are talking about potentially millions of dollars being drained and possibly a crash across the cryptocurrency market as confidence over DeFi gets hit.
In step 4 & 5, MakerDAO assessed the validity of the vulnerability. In this case, MakerDAO got the help of HackerOne to triage the vulnerability. Eventually, they acknowledge the finding as valid and released a fix to patch the vulnerability.
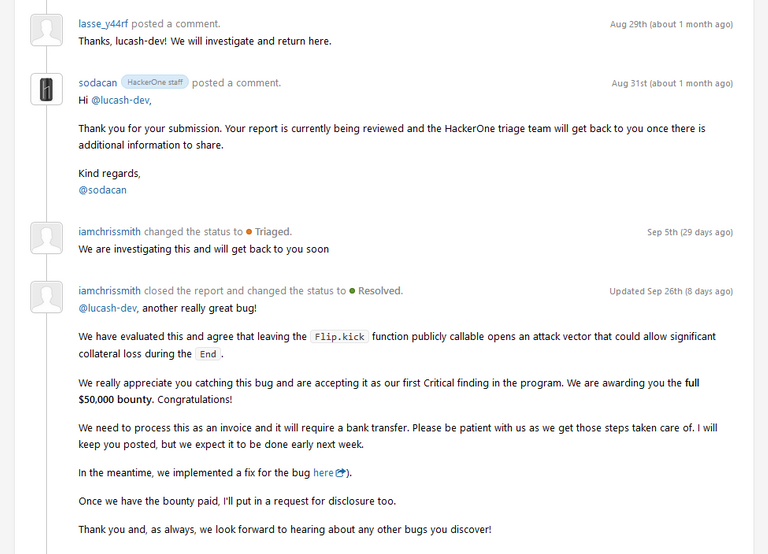
Then comes steps 6, 7 and 8. The bounty hunter checked that the fix is effective to patch the vulnerability before disclosing it to the public. This is aligned with the bug bounty program disclosure policy,
"The reporter allows the Maker team a reasonable amount of time to fix the vulnerability before disclosing it to other parties or to the public".
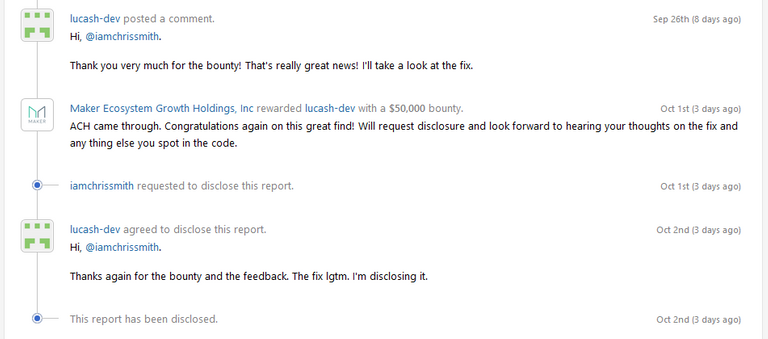
At the end of the day, the bounty hunter acknowledged that the fix is effective and went ahead to disclose the vulnerability to the public and that is how we got to know about it.
Conclusion
In this case, a $50,000 bounty saved MakerDAO and potentially the entire cryptocurrency market. This shows the importance of performing independent security assessments before putting any systems live. As a holder of DAI, I am grateful that this was discovered before MCD was deployed to the mainnet. It could have been a catastrophic event if collateral are drained and stolen.
Drawing comparison with Steem. Now with the Steem Proposal System (SPS), we can easily setup bug bounties for upcoming hardforks or any Steem related projects. This will help draw some interests from bounty hunters who are not aware of Steem and also improve the security of Steem ecosystem. It is always good to gain some external attention and improve our security. I hope to see such proposals eventually.
The "Raise to 50" Initiative
Under 50 SP and finding it hard to do much on this platform? I might just be able to raise your SP to 50. Check this post to find out more!
This article is created on the Steem blockchain. Check this series of posts to learn more about writing on an immutable and censorship-resistant content platform:
Congratulations @culgin! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Vote for @Steemitboard as a witness to get one more award and increased upvotes!
Very interesting read!
Thanks!
Hi @culgin!
Your post was upvoted by @steem-ua, new Steem dApp, using UserAuthority for algorithmic post curation!
Your UA account score is currently 4.037 which ranks you at #3884 across all Steem accounts.
Your rank has not changed in the last three days.
In our last Algorithmic Curation Round, consisting of 90 contributions, your post is ranked at #45.
Evaluation of your UA score:
Feel free to join our @steem-ua Discord server
!trdo
Congratulations @hobo.media, you are successfuly trended the post that shared by @culgin!
@culgin got 2.25563400 TRDO & @hobo.media got 1.50375600 TRDO!
"Call TRDO, Your Comment Worth Something!"
To view or trade TRDO go to steem-engine.com
Join TRDO Discord Channel or Join TRDO Web Site
It's a very innovative program that looks for errors in parallel.
I suppose these error hunters must have good intentions, as they are supposed to.
I guess the verification work after reporting the bug should be an easy process to handle. To prevent the informant from losing patience. As you say, it depends on how substantial the reward is.
pd: I support implementation in steem
@culgin, Some steps are important to take which will going to prevent Catastrophic Event. Good to go through from your blog and in my opinion these kind of events can teach budding projects. Stay blessed.
Posted using Partiko Android