Ethnographic origin of cryptanalysis

From a scientific theoretical construct, cryptanalysis is nothing more than the study of cryptographic systems in order to find weaknesses in the systems and break their security without the knowledge of secret information, it is important to note that the methods and techniques of cryptanalysis come from cryptoscience.

Fig. 2 The methods and techniques of cryptanalysis are derived from cryptoscience. Image of public domain, Author: Vector_Studio, 2020
Cryptoscience is understood as the scientific segment that studies algorithms, protocols, and each of the systems used to protect valuable information, with the purpose of conferring greater security to the growing flow of communications and exchange of documents and data.
While assigning keys, encrypting (hiding the content of a message from the naked eye), designing codes using mathematical algorithms are an integral part of our lives, and especially for those of us who make use of the web 3.0, it is important to emphasize that these methods were devised by Julius Caesar, military leader, politician and dictator of the last era of the Roman Republic.
According to ethnographic scientific reports, after Julius Caesar reached the peak of power and became the key figure of the Roman Empire, in order to keep secrets for a while, he invented the shift cipher, basically this method devised by Julius Caesar was a simple substitution cipher, which consisted of replacing all the letters by other letters of the alphabet.
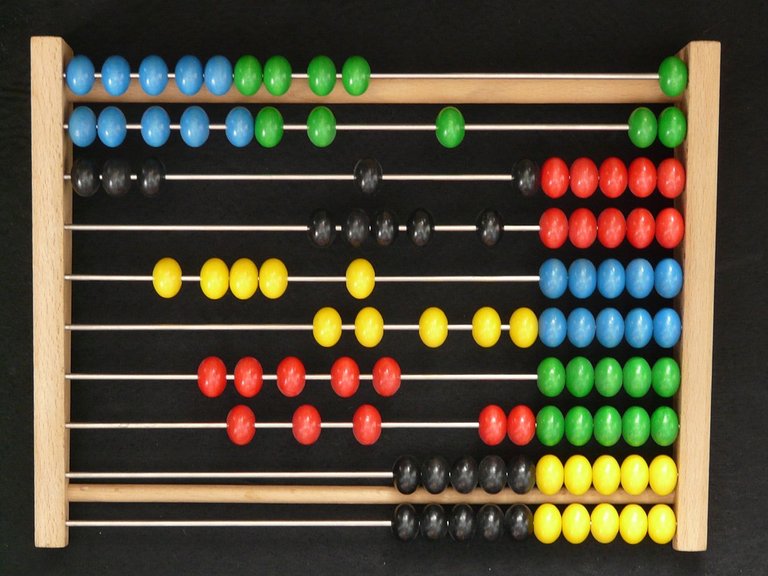
Fig. 3 The method devised by Julius Caesar was a simple substitution cipher, which consisted of replacing all the letters with other letters of the alphabet. Image of public domain, Author: Hans, 2011
After displacement encryption, an infinite number of encryption methods emerged, including the cryptographic technique of the Spartans, Freemason encryption, among others of lesser or equal relevance up to our sophisticated computational methods and the creation of keys by means of the computer cryptosystem.
BIBLIOGRAPHICAL REFERENCES CONSULTED:
[1] Onwutalobi A Overview of Cryptography. SSRN Electronic Journal. 2011. Article: Online access
[2] Chandrasekhar R Cryptography and network security lecture notes. Article: Online access
OBSERVATION

0
0
0.000
Very informative piece. Thanks
Hi @valchiz, thanks for leaving your appreciation. Best regards, be well.
Hi @lupafilotaxia Trying to decipher the encrypted messages is a real art that requires very deep knowledge, I did not know your publication led me to investigate in addition to your contribution, really very interesting, success.
Hello @aplausos
Correct decrypting encrypted messages is a real, thank you for leaving your positive comment, good that the article is useful for you.
Best regards, be well.
I am new to this Crypto space , and currently I am learning new things this is something new I have learn Today and will be glad to learn more from your post in future.
Hi @genx-miner
Thank you for leaving your positive comment, wrb 3.0 gives us this possibility to access multidisciplinary information.
Best regards, be well.