Cellebrite Can "Hack Any Device" with UFED Extraction Technology | DD18 The Wikileaks Archive
In 2015, the FBI demanded that Apple provide access to the iPhone of the San Bernardino shooter after the perpetrators killed 14 in a mass shooting and wounding 17 additional people.
Apple refused to cooperate arguing that allowing law enforcement access to their code would compromise the privacy of its customers and also undermine the company's brand and image.
Apple did not provide a backdoor to their encryption. Nevertheless, in a matter of weeks the FBI had 'hacked' the San Bernardino shooters device with the help of a private company.
The company who was able to break Apple's encryption was an Israeli tech company established in 1999 called - Cellebrite. Though, the identity of the company was not disclosed at the time, the Israeli company would come to prominence in the tech world for it's ability to "hack any device" gaining notoriety and a long list of new clients.
Wikileaks Archive
https://shoppinglist.wikileaks.org/docs/pa_19PM0718Q0010JOFOC
https://shoppinglist.wikileaks.org/docs/pa_19PM0718Q0010
Panama Embassy Request for UFEDs
UFED = Universal Forensic Extraction Device
In 2018, Wikileaks released a trove of approximately 16,000 correspondences from US embassies around the world. This collection is known as the - Embassy Shopping List.
A cable from the Panamanian embassy titled:
Justification And Approval (J&A) For Other Than Full And Open Competition
puts out an open bid contract to procure 7 UFED licenses for Cellebrite equipment to be used to combat drug trafficking in coordination with the Government of Panama (GOP).
The purpose of this requirement is to activate the currently owned Cellebrite extraction devices to aid in support the Government of Panama's (GOP) vetted unit law enforcement divisions to be able to pull information out of phones and identify information that can assist in maintaining national security for Panama and the US.
The Office of Management and Acquisitions sought the licenses to continue the use of the current Cellebrite devices used in operations in Panama. Furthermore, the email stated that the (procurement) was temporary as newer models of Cellebrite UFEDs or UFEDs equal to Cellebrite in capability and price were acquired in the near future. The cable goes on to state that agents are already familiar with the Cellebrite software which they use to gain access to the devices criminals involved in drug trafficking.
Extraction devices allow the Vetted Units to quickly download information from cell phones when a person is detained to aid in identifying counterparts in drug trafficking, migrant trafficking, and transnational criminal organizations. When defendants are arrested, they often are in possession of several cellular phones, providing a rich source of information in the coordination of criminal activity in Panama, the region, and the US. Cellebrite is a copyrighted company providing certified licenses and equipment to perform the extractions and the Vetted Units already have the training and proficiency in using this brand of device and their systems are integrated to this particular software.
In line with open bid government contracts, the embassy identifies several potential sources for obtaining the licenses required to perform extractions with authorized Cellebrite software providers.
- Cellebrite (US)
- Digital Shield (US)
- H-11 Digital Forensic (US)
- Health Tech Innovation (Panama)
Digital Shield, also Digital Shield Incorporated (DSI), boasts a long list of government agencies as clients including the: NSA, FBI, FAA, Department of Defence, State Department and Customs and Border Protection.
DSI is "dedicated to assist in the response, discovery, analysis, mitigation and tracking of cyber incidents as they occur within commercial and government entities."
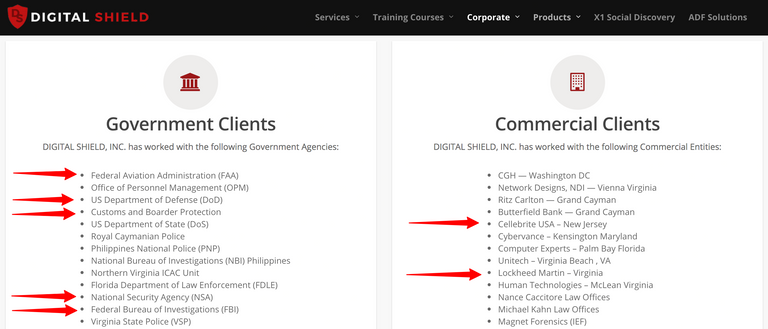
Equally, H-11 Digital Forensics describes itself as a global leader in digital forensics technology. A banner on the company's website boldly states - "Find the Exploit".
WHY?
While coordinating anti-drug trafficking operations with US allies is commonplace, there's very little information as to who the "Vetted Units" trained Cellebrite software are and why the US Embassy is procuring and/or importing devices that essentially amount to spy equipment.
It is widely known that US embassy official positions provide cover for Intelligence Agencies and their operatives. Furthermore, aid agencies such as USAID have long been used for identical purposes.
UFEDs

source
As terrorist organizations and organized crime become more high tech as do the methods to counter criminal activity. Universal Forensic Extraction Devices are fast becoming a preferred tool for law enforcement and intelligence agencies worldwide.
Generally speaking, many people believe that the security of their mobile devices locked with a pin, password, fingerprint or biometric ID is sufficient to secure their devices. In reality, UFEDs are powerful tools employed to access an individual's private information and correspondences and are extremely invasive machines posing serious legal and ethical questions.
UFEDs allow the government to access the vast troves of data contained in cell phones. These devices connect to your phone and download all of its contents – from your contacts list to your location data – within seconds. Their software breaks or bypasses passwords, “unlock” codes, and other security features.
How it works
They Are Watching is a privacy advocacy website that monitors threats to privacy and invasive technologies such as Cellebrite. The following infographic demonstrates how Cellebrite is used to extract ALL data from any device.
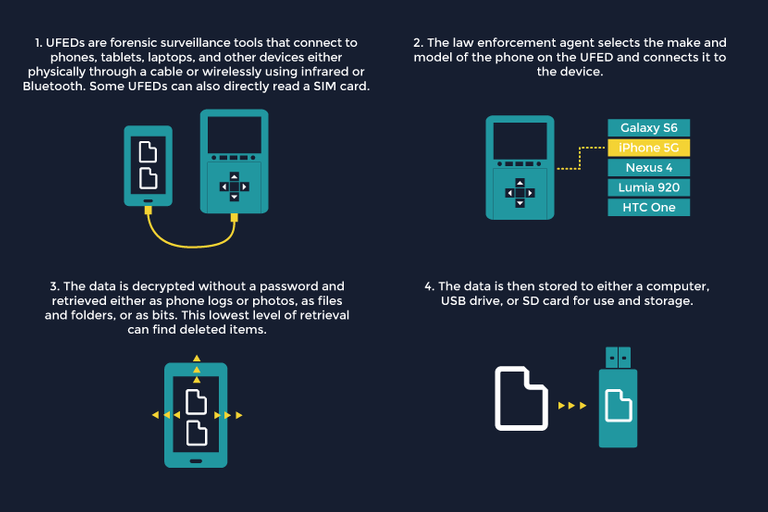
Cellebrite has the ability to extract: passwords, SIM/USIM data,files, photographs, contacts, and meta data from any device regardless of the manufacturer.
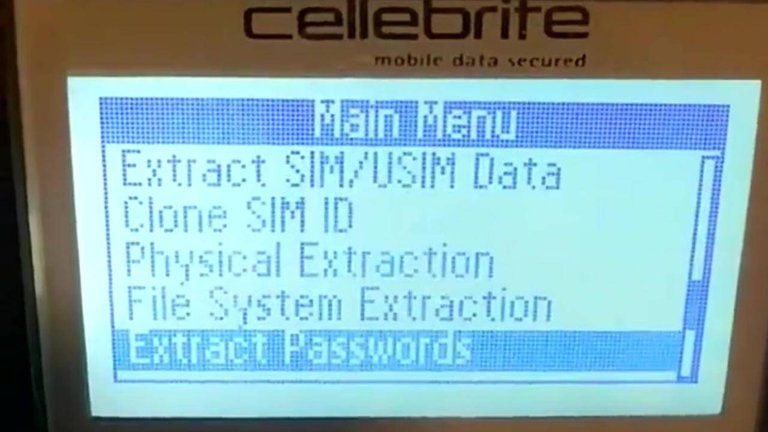
Perhaps the most disturbing feature of Cellebrite, is its ability to CLONE SIM identification. This feature has a number of dubious implications when this function is used in relation to law enforcement activities, intelligence gathering or when wielded by private companies, individuals or even criminal organizations.
Cellebrite

cellebrite.com
Cellebrite is an Israeli tech company founded by Yossi Carmil and is an acting co-CEO with his counterpart Ron Serber. Cellebrite promotes itself as a digital intelligence solutions company.
As previously mentioned, the company's profile was elevated when it was identified as the secret Israeli firm able to penetrate Apple's encryption systems by assisting the FBI in cracking the San Bernardino shooters iPhone in 2015.
Before joining Celebrite as CTO in 2001, Co-CEO Ron Serber was previously the director of software development with Pegasus Technologies a CIA-controlled entity.
A 2016, the Intercept reported that the company actively recruited from UNIT 8200 the Israeli Defense Force elite hacker group.
In interviews discussing the significance of the company's signature UFED, Mr. Carmil has been upfront about its powerful penetration capabilities.
“These toys, these handsets, today are basically reflecting everything about the phone owner’s personality,” says Cellebrite CEO Yossi Carmil. “There is a lot of data inside which tells everything about a person.”
Haaretz
One would assume that Apple, and other smartphone manufacturers, would be up in arms about a rival tech company that specializes in cracking their security protocols. Instead, many leading tech companies, including Apple and Samsung, are satisfied customers of the Israeli firm.
“There’s a clear conflict between us, who seek to allow investigators to obtain evidence to keep the public safe, and an organization that advocates privacy protection. But at the end of the day, I sleep well because I know for whom I work and what values I serve. I guess the smartphone makers are happy too because otherwise, the regulators would have found other ways to force them to disclose the information.”
Cellebrite’s ability to penetrate cellular devices brings to mind another Israeli company, NSO, which is capable of hacking people’s phones without their consent.
ynetnews.com
It appears that companies like Apple are content to have their devices breached by a third party because it allows the smartphone manufacturers to maintain that they did not, and do not, willingly provide access to their devices to law enforcement.
While industry leaders appear willing to cozy up to Cellebrite, human rights organizations caution that these encroaching technologies assist authoritarian regimes in silencing criticism and dissent.
Carmil resents the comparison: “I know the people at NSO and appreciate their know-how, but Cellebrite works in the legitimate world of the police force, whose abilities are closely controlled, unlike the world of NSO customers and others who engage in illegal and concealed. Cellebrite is totally on the good side, where court orders are used. We do not make tools for breaking into private entities or espionage organizations.”
Amazia Keidar, Cellebrite’s VP of international marketing, says the Cellebrite story is as an Israeli success story as the Waze or Mobileye story.
Of course, the proprietors of the technology will offer only a glowing review of their trademark product and claim that its users are held to the highest of standards. However, Cellebrite has already been used by authoritarian regimes to breach the devices of journalists resulting in their imprisonment.
Journalists Imprisoned in Myanmar
The quasi-democratic military dictatorship in Myanmar used Cellebrite to crack the phones of two journalists reporting on the 'ethnic cleansing' of more than 1 million minority Rohingya Muslims in the country. The pair faced 14 years in prison under the Official Secrets Act in the South East Asian nation.
The Times of Israel reported that repressive regime in Myanmar is a major customer of Cellebrite despite the companies claims that it aims to, “uphold the standards of international human rights law”. In rare instances, the company may revoke its sales and services to those that do not comply with their standards. Following reports that their technology was being misused by Myanmar the company stated that they suspended sales to the regime months before the incident took place. Israel has admitted that it has sold "advanced weapons" to Myanmar in the past but maintains that this practice was halted in 2017.
Times of Israel
The two reporters were sentence to 7 years in prison by a Myanmar court but were subsequently released in 2019 bowing to international pressure.
Cellebrite Integration for COVID-19
Reuters recently reported that Cellebrite software could be used by law enforcement for tracking the spread of COVID-19.
When someone tests positive, authorities can siphon up the patient’s location data and contacts, making it easy to “quarantine the right people,” according to a Cellebrite email pitch to the Delhi police force this month.
Reuters
Contact tracing software is being pushed by governments and tech industry representatives around the world as key component in combating the spread of COVID-19. Yet, privacy rights activists are not convinced and argue that these invasive technologies have serious potential for abuse and violate personal privacy as well as rights to free movement. Although the company maintains that it respects individual privacy, it admits that there are instances where police hacking of devices is warranted.
While this would normally happen with a user's consent, Cellebrite said that there are legally justified cases in which police could use their tools to break into an acquired device — such as if an iPhone is confiscated when someone violates public gathering orders. "We do not need the phone passcode to collect the data," the Cellebrite spokesperson said in the pitch email.
The Cellebrite pitches are just part of a new wave of private intelligence and surveillance companies attempting to repurpose and sell their tools to law enforcement to track the virus and enforce stay-at-home orders, according to Reuters.
Once more, the Israeli tech company argues that law enforcement is legally justified in extracting ALL data from a device for individuals who "violate public gathering orders". This would include protests, those not following social distancing decrees or those that attend unauthorized community events.
Cellebrite and Pre-Crime AI

Perhaps one of the most disturbing trends emerging from the world of private security and technology is the development of Pre-Crime Artificial Intelligence enterprises. This is another avenue Cellebrite is actively pursuing. As a matter of fact, co-CEO Yossi Carmil insists that the company is already nearing the point where it will be able to actually predict crimes before they occur.
According to Carmil, we are on the verge of a new era of "digital policing" that incorporates deep machine learning and predictive analytics.
Drawing from a vast stream of data sources: smartphones, smartwatches, smart TVs, smart cars, smart homes, smart meters, PCs, drones, an array of street level cameras, and the internet of things, the ability to access unfathomable amounts of data will allow processing power and analysis that will far surpass human capabilities. From this enormous pool of data, predictive analytics will be able to identify potential criminals an notify its 'customers'.
In the words of Cellebrite's Yossi Carmil:
“There is an ocean of information out there; petabytes of data. We tend to the entire digital stream: extract the digital information, release it, lock it, decipher it, gain access to it, process and compile the data into a pile of evidence and then make sense of the information and manage it. Today’s police forces need a far smarter digital stream. Cellebrite helps them with digital policing. We estimate our technologies help the police solve nine out of ten cases.”
Furthermore,
Cellebrite’s machine learning system can detect code words and hints that suggest such eventualities, point to criminals that might be involved in a specific event, locate weapons in databases on thousands of images and conclude their location, and more.
These are bold predictions in themselves. It's unclear how the technology would 'detect code words and hints' accurately and exactly how these determinations will be made. We are assured that the private company's algorithms will draw from various data pools suggesting that this ensures accuracy.
Still, there are other determining factors that could have serious impact on human lives. There's no mention of bad data or built in bias of AI algorithms.
The head of Google's AI program, John Giannandrea, warns that a persistent danger to any AI system are biases that are baked into the technology, sometimes unconsciously.
“The real safety question, if you want to call it that, is that if we give these systems biased data, they will be biased
technologyreview.com
In a nutshell, when AI system inputs are fed bad data they will produce flawed results.
Carmil seems unconcerned with potential pitfalls choosing to instead focus on the company's unique capabilities. He continues:
“Our analytical tool exceeds all analytical tools offered by others because we rely on high-quality information, which other companies cannot obtain. In Thailand, for example, we stopped human trafficking with our capabilities. The police were able to stop a specific truck on the border crossing, lift the tarpaulin cover, and discover the chained women and children transported to be sold for prostitution.”
Strikingly, Carmil boasts that his company has access to "high-quality information, which other companies cannot obtain." It seems as though he may be referring to information gathered with unorthodox methods. It's likely he's referring to data provided by extraction devices, which is Cellebrite's specialty.
Considering that the company is a pioneer in breaking into people's devices and extracting everything from them;
Who would not have some sort information that could be used against us?
When you know every tiny detail about someone, do you not have the ability to control them completely?
Is it possible to inflate criminality in order to justify the value of a particular brand of software and ultimately its profitability?
This are serious ethical questions that should be discussed in the public sphere and not determined by technocrats in their silo-ed communities in Silicone Valley and Tel-Aviv.
Cellebrite Hacked in 2017

A final concern regarding the use of UFEDs is that once the data has been extracted and stored for analysis it too is vulnerable to hacking.
In 2017, Cellebrite announced on its website that an "external web server" had been breached. More specifically, the company clarified that a "legacy database backup" had been hacked which reportedly contained basic contact information and hashed passwords of some of customers.
Despite company assurances that it did not know of any "any specific increased risk" to its clientele, it is believed that over 900 gigabytes of data pertaining to Cellebrite had been compromised.
The data cache contains more than just customer information, with technical data about Cellebrite's products and evidence files from seized mobile phones allegedly included in the haul, though it is unclear if details of device vulnerabilities were present.
appleinsider.com
The hack of the database highlights how personal private data extracted by 'licensed' law enforcement agencies by hackers who, in turn, accessed data safeguarded by the leading digital forensic extraction company, is not only ironic, but it adds to a long list of concerns regarding this contentious technology. This demonstrates how even the most tech savvy security companies are also vulnerable to extraction which further endangers people's private data who may or may not have committed any crime aside from gathering in their own communities.
Moreover, it brings into question how any of the data accrued by Cellebrite can be secured.
In Conclusion
UFEDs are already being employed by law enforcement and intel agencies worldwide and this trend is only going to increase as the technology is applied to a wider range of police operations.
As we have seen, the technology is scheduled to be put to use for COVID19 contact tracing and tracking of individuals who gather in large groups such as protesters.
While these technologies are being rolled out, it's critical that we take a long hard look at whether or not they actual provide more benefits to society than they do harm.
A final crucial element is that though these digital forensic developers claim they uphold only the "highest standards" in coordination with the law, their software is private and not subject to oversight. There's no way of knowing if a company like Cellebrite, and it's proprietary algorithms, are objective and unbiased.
As Google's AI chief Giannandrea affirms:
“It’s important that we be transparent about the training data that we are using, and are looking for hidden biases in it, otherwise we are building biased systems,” Giannandrea added. “If someone is trying to sell you a black box system for medical decision support, and you don’t know how it works or what data was used to train it, then I wouldn’t trust it.”
Sources
https://appleinsider.com/articles/20/04/28/cellebrite-pitching-iphone-hacking-tools-as-a-way-to-stop-covid-19
https://www.cbsnews.com/news/leaking-at-all-costs/
https://theintercept.com/2016/10/31/fbis-go-hackers/
https://www.ynetnews.com/articles/0,7340,L-5618901,00.html
https://theyarewatching.org/technology/forensic-extraction
https://www.cellebrite.com/en/home/
https://www.timesofisrael.com/israeli-tech-used-to-imprison-journalists-in-myanmar-report/
https://www.haaretz.com/israel-news/business/.premium-inside-the-israeli-company-that-can-crack-the-iphone-1.5420595
https://www.reuters.com/article/us-health-coronavirus-spy-specialreport/special-report-cyber-intel-firms-pitch-governments-on-spy-tools-to-trace-coronavirus-idUSKCN22A2G1




I remember when researching the blackphone and that even though it's so privacy-centric, it's still not very private at all because:
Between something like that, the keyloggers, and the various permissions that all the apps require, I've given up the idea that anything done on cellphones can be done privately and it's probably just as bad with computers too. Most, any-and-all privacy, is illusory at best.
You'll get a series of dark patterns to keep you under the illusion that your data is yours and private, but it's simply not true in most cases. If you want privacy on a cellphone; cut out the microphone and camera, remove the battery, chuck it inside of a Faraday bag. Gently place said bag in a microwave, and then throw that off the nearest cliff.
LOL, great advice!
Good to see that many protestors are leaving their phones at home.
I wasn't able to fit it into this article but I do believe that UFEDs mainly use exploits inside some of the most popular apps in order to bypass security.
Waaaaaaaaaay too much power in any one person's hands. No wonder the state wants total control over such technologies. The average person doesn't stand a chance against that kind of invasive power. Scary that it was old news a few years ago (in certain circles). Us regular people could only imagine such things. I did. I got called crazy and paranoid for it.
Every device you buy is compromised at the factory. Every act is scrutinized.
Don't sell drugs. Don't carry a tracking device on you.
When you can print your own, then you can carry a phone. When you can prevent assault by armed brigands, then you can sell drugs safely. Until then, you're taking your life in your hands if you do carry your phone with when you're dealing drugs.
Just don't.
Backdoors do exist in most of the big tech devices, and there are six ways to Sunday to compromise our devices.
And yeah, if you're going to protest, it might be a good idea to leave these tracking devices at home and any medicinal medicines as well ;)
Crazy...just last week one dumb fart was arguing with me that Iphone was unhackable.
Yeah, that was proven to be false years ago. lol
very nice one! I have been thinking of it. Cellebrite could be used to monitor every single person using the excuse of COVID19. That's disgusting and I will always refuse to install any shit app.
Everything is hackable, Starting with the fact that the towers monitor all our devices.
Oh for sure, I don't disagree.
I think that Cellebrite allows unskilled law enforcement officers a fast and easy way to get the personal data of anyone they arrest.
Always appreciate your investigations.
A little off topic, but was hopeful you might have come across this. I knew vaguely about the stingray interceptors being used to intercept cell phone communication between cells and towers. On a thread the other day, one of the protestors said authorities used one to zap everyones cell phone batteries dead. Have you heard of such a thing? I spent hours trying to find any indication they can do that and found nothing.
That's really interesting, and no I hadn't heard about this. I didn't know that stingrays could be used offensively like that, I thought they were only capable of intercepting signals. I heard that jammers were being deployed by some police departments though. If you find anything more about that certainly make a post in deep dives as I think that highlighting the tools being used to put down legitimate protests is valuable information.
Hacking any device seems quite pretentious. Especially that now we have phones running linux where countless security tools are available.
That's how the company promotes their product and from what I understand about the intel agency related company they're focus is on mobile/smartphones predominantly. Access to PCs/laptops is usually gained through cloud synching with the mobile device.
But yes, the "hack any device" may be somewhat overblown but it is how their UFEDs are advertised to law enforcement agencies.
Very good, I read almost 1000 words in your post, but unfortunately I do not understand anything about the contents of this story, because I do not understand about UFED / that you discuss, but this is a good story and useful thanks
Man this one was another excellent post. I learned a lot about these nefarious companies and how privacy is pretty much gone. Not that I didn’t think it was gone already before this lol.
I think that the sim clone is indeed a crazy thing they can do! Make phone calls from a cloned sim that no one would be able to tell since they can mimic a voice with a computer too.
Makes you think what the hell the deep labs at the pentagon are working on if this is in the public now? Ugh!
good game
well played
Wow, Wikileaks has done a great job letting us know these exist.
Yeah, they're not widely known in the public but they are well known in the field of intel and law enforcement. Perhaps another reason to leave your phone at home from time to time ;)
Congratulations @v4vapid! You have completed the following achievement on the Hive blockchain and have been rewarded with new badge(s) :
You can view your badges on your board And compare to others on the Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPDo not miss the last post from @hivebuzz:
Support the HiveBuzz project. Vote for our proposal!
I wish to join the Deep Dives Community and do some writing but I'm scared 😫😩. I Officially joined few weeks ago but very scared. Can you please put me through my Friend @v4vapid
Excellent reporting.
Cheers, thanks for having the patience to read it ;)